Edwards normal form
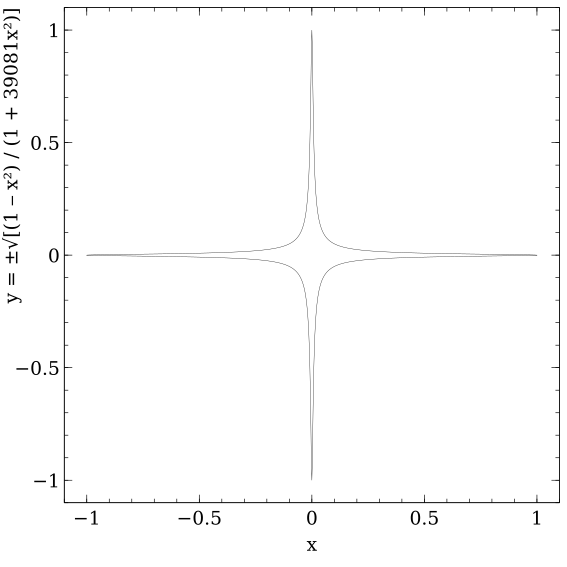
Elliptic curve known as Ed448 “Goldilocks” in Edwards normal form with
An elliptic curve is in Edwards normal form[1] if it can be described by the equation
The more general original Edwards form has another parameter c
but it is very simple to eliminate the scale parameter c and reduce this equation to its normal form for ease of performing algebraic group operations on rational points or finite fields.
The twist
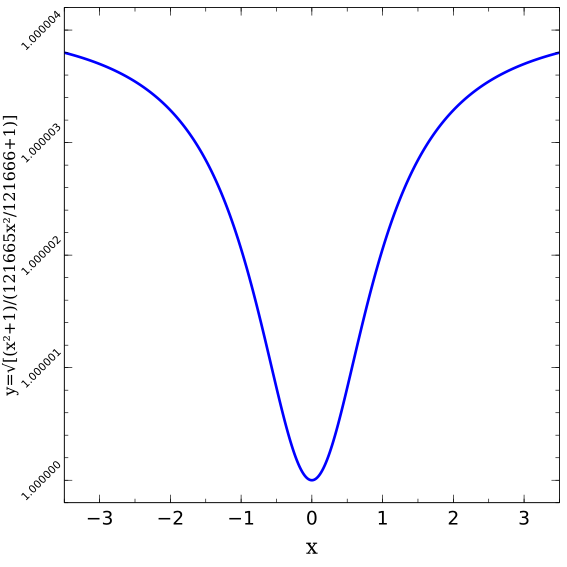
This elliptic curve in a so-called twisted Edwards form is the one used in the Ed25519 digital signature scheme [2].
There is also a “twisted” Edwards form
And this brings us back to the ancient Greek word στραγγός with the idea of using something “twisted” for strong cryptography.
Point group arithmetic
The point group operation on an elliptic curve in the twisted Edwards form as defined above is defined as [3]
- .
Protestants find it offensive to refer to arithmetic or other operations as of some “law” or as works done through or under the “law” so to speak, although that term does appear as such in the original literature. It is something vaguely felt to be grammatically repulsive, almost as if in Spanish to imply, “bajo la ley” and not “sobre la ley” or above-board.
The term “law” is normally reserved in mathematical contexts for a formal probability measure over an event space. The abuse of the term in the cryptologic literature (hint, hint, there’s an arbitrary “law” involved in a mathematical operation) cannot be a coincidence. The FBI under Christopher Wray has for many years, and under other directors as well, been demanding “lawful access” to break the aforementioned encryption at will, and as usual, it’s “for the children” [4][5].
- ↑ Harold M. Edwards. “A normal form for elliptic curves.” Bulletin of the American Mathematical Society, vol. 44, no. 3, Jul 2007, pp. 393–422. https://www.ams.org/journals/bull/2007-44-03/S0273-0979-07-01153-6/
- ↑ Wikipedia: EdDSA https://en.wikipedia.org/wiki/EdDSA#Ed25519
- ↑ Daniel J. Bernstein, Peter Birkner, Marc Joye, Tanja Lange, and Christiane Peters. “Twisted Edwards Curves.” Cryptology ePrint Archive, vol. 2008, no. 013 https://eprint.iacr.org/2008/013.pdf
- ↑ Christopher Wray, Director Federal Bureau of Investigation. “Finding a Way Forward on Lawful Access: Bringing Child Predators out of the Shadows: Remarks as delivered.” Department of Justice Lawful Access Summit, Washington, D.C. October 4, 2019. https://www.fbi.gov/news/speeches/finding-a-way-forward-on-lawful-access
- ↑ Zack Whittaker. “US attorney general William Barr says Americans should accept security risks of encryption backdoors.” TechCrunch, July 23, 2019. https://techcrunch.com/2019/07/23/william-barr-consumers-security-risks-backdoors/







